Phishing attacks
Definition
a technique that uses social engineering and spoofing to obtain the target's information.
a phishing email pretends that it comes from a legitimate place (your bank or your social account) and ask you to provide an action like:
a phishing email pretends that it comes from a legitimate place (your bank or your social account) and ask you to provide an action like:
- Giving personal information: phone number, location, etc.
- Credentials submission: username or password, etc.
- Click a link that goes to a login page
- www.faceb00k.com/login.php
- www.paypel.com/password-recovery
so you should pay attention to the URLs spelling, in fact, a good practice is to never click on a link from an email, instead, you can type the URL by yourself directly in the search bar.
target's local machine (needs access to the target's machine)
Ex: when the client search for realWebSite.com, he will be redirected to 5.5.5.5 (the bogus site) instead of 10.10.135.11, the is known as DNS spoofing.
this is a dangerous attack if it's combined with phishing because the attacker isn't required to change the URL spelling, therefor the anti-malware won't detect a thing (everything will look normal)
There are many other variations of scams that use phishing: Advance-fee scam, Boss/CEO scam phone verification scam, etc, you can find some great summaries on Reddit
Tricks to a successful phishing
- we already mentioned the usage of typosquatting www.facobook.com or prepending a letter and hope that the target doesn't notice it www.ffacebook.com
- Reverse engineer the design of the targeted web page so that it looks exactly like what you supposed to see
- pretexting you with true information about you to make you relaxed about the email, saying for example that the monthly payment of your Netflix is in-place and that they need the Visa card verification to proceed with it, you will be surprised about how much information is available on social media and on the internet about you (this is known as OSINT).
Phishing Types
Pharming
Redirecting the target to a bogus site by poisoning the DNS server or by altering the hosts file intarget's local machine (needs access to the target's machine)
Ex: when the client search for realWebSite.com, he will be redirected to 5.5.5.5 (the bogus site) instead of 10.10.135.11, the is known as DNS spoofing.
this is a dangerous attack if it's combined with phishing because the attacker isn't required to change the URL spelling, therefor the anti-malware won't detect a thing (everything will look normal)
Vishing
known as voice phishing, this method relies extensively on social engineering, this attack is very common due to the simplicity of gathering Caller IDs, another way of doing this is using SMS or what we call Smishing.Spear phishing
target a specific individual within the organisation by simply gathering more information about him, this type of phishing take more time then non-targeted one, because the goal here to garantee that the victim believes the email's legitimacy, this attack often targets the CEOs and CFOs, aka Whaling (going after the biggest fish in the organisation), this is why it is crucial to teach those individuals about this attacks and constantly run phishing tests on them.There are many other variations of scams that use phishing: Advance-fee scam, Boss/CEO scam phone verification scam, etc, you can find some great summaries on Reddit


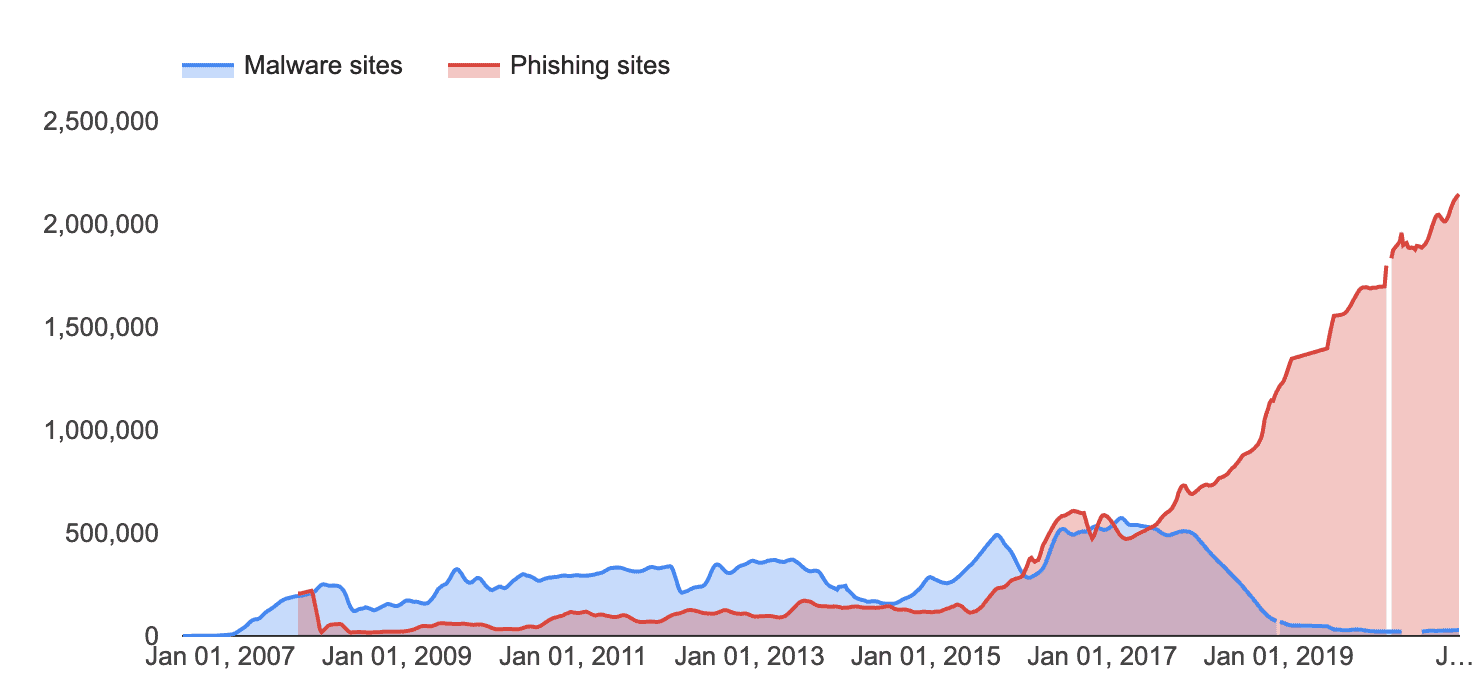


Comments
Post a Comment