Wireshark for Security Analysis | Filter for unusual DNS packets
This is a quick exercise to practice the previous information mentioned in the Wireshark customization article
Download the pcap file from here and try to answer the following questionsQuestions
- How many UDP/TCP conversations do you see in this pcap?
- How many DNS conversations do you see in this pcap, and How many of them are malformed?
- How many DNS responses do you see?
- Do any of the responses have more than 100 answers? Can you set and save a filter for this activity?
- What is the packet with the most Answer RRs?
- How many UDP/TCP conversations do you see in this pcap?
Answers
- How many UDP/TCP conversations do you see in this pcap?
Statistics > Conversations

- How many DNS conversations do you see in this pcap, and How many of them are malformed?
Statistics > Protocol Hierarchy

- How many DNS responses do you see?
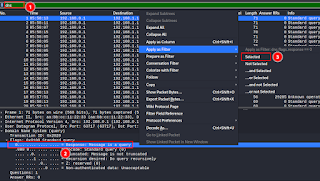
Filter for DNS > choose any packet > Right-click on the Response flag > Apply as a Filter > Selected

look at the bottom of the screen

- Do any of the responses have more than 100 answers? Can you set and save a filter for this activity?
Choose any packet > Right-click on the Answer RRs > Apply as a Filter > Selected
modify the filter to “dns.count.answers > 100” > + button > name it > ok

- What is the packet with the most Answer RRs?
Right-click on the Answer RRs > Apply as a Column > sort by its value





Comments
Post a Comment