Vulnerability management Lab | Nessus Essentials
What is it?
Vulnerability assessment or vulnerability management is a process of analyzing an organization's systems for possible security flaws. It runs a vulnerability analysis to see if the organization is vulnerable to known vulnerabilities, provides a severity level to those vulnerabilities, and suggests if the danger should be mitigated or remediated.
Vulnerability testing aids organizations in determining whether their systems and software have insecure default settings, such as admin passwords that are easily guessable. It also checks for a potential escalation of user rights or faulty authentication procedures, as well as vulnerability to code injection attacks such as SQL injection (SQLi) and cross-site scripting (XSS). fortinet.com/resources
Types of Vulnerability Assessments
The following are the most prevalent types of vulnerability assessments used by businesses:
- Network scan: Identifies susceptible systems on an organization's wired and wireless networks that could be leveraged to launch security attacks.
- Host assessment: The assessment of critical servers, which may be vulnerable to attacks if not adequately tested or not generated from a tested machine image. imperva.com
- Wireless scan: Typically checks an organization’s Wi-Fi connections to seek for any rogue access points (APs) and validate whether the network is configured securely.
- Application scan: Examines a company's websites for known software flaws and insecure setups in web apps or networks.
- Database scan: Detects flaws in databases and large data systems, such as misconfigurations, rogue databases, or unsafe development environments, in order to safeguard businesses from harmful assaults.
The Lab
Downloads links:
- Nessus Essentials https://www.tenable.com/products/nessus/nessus-essentials
- Windows 10 ISO https://www.microsoft.com/en-us/software-download/windows10
- VMWare Workstation Player https://www.vmware.com/products/workstation-player/workstation-player-evaluation.html
Nessus Essentials:
or you can install it directly from the Linux terminal
sudo apt install nessus
then you should start the Nessus service (not needed on Windows)
sudo systemctl start nessusd.service
then open the browser and go to https://localhost:8834/
Select Nessus Essentials
next, start the VM and install Windows; You can use the instructions used in this lab here
if you have any problems, feel free to ask in the comments section below
give a name for the account and a relatively easy password to test it later
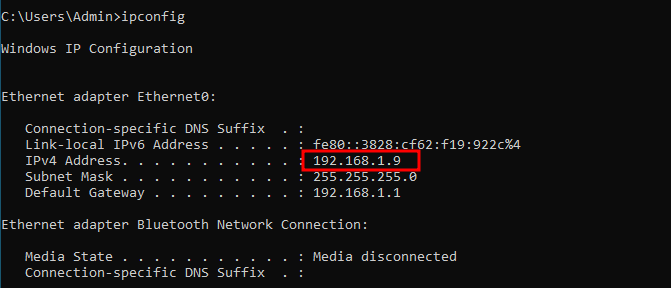
as you can see, the ping is not reaching the VM, so we must disable the Windows Firewall for now
Start menu > search for wf.msc
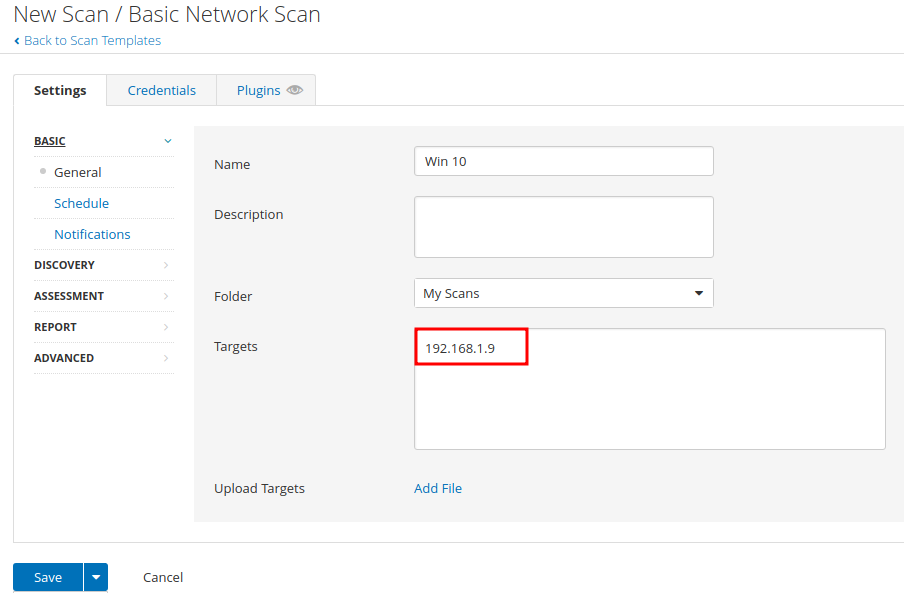
Basic Network Scan
Credentialed scan:
we need to enable remote registry service on Windows
Start menu > search for services > Remote Registry > double click > manual > apply > Start > Ok
Disable User Account Control, based on this article from tenable: tenable.com/Scanning-with-non-default-Windows-Administrator
Start menu > User Account Control Settings > never notify > Ok
next, locate the following registry subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\LocalAccountTokenFilterPolicy
If the LocalAccountTokenFilterPolicy registry entry does not exist, please follow the steps below to create it:
- On the Edit menu next to the registry keys, perform a "Right-Click" and click on "New".
- Click on "DWORD (32-bit value)"
- Either the name of the new DWORD to LocalAccountTokenFilterPolicy .
- "Right-click" on LocalAccountTokenFilterPolicy and then click "modify".
- In the Value data box, type 1, and then click OK.
- Exit Registry Editor.
- Restart the Virtual Machine
Start the scan
go back to Nessus > click on New Scan > same Settings as before > Credentials > add the VM's username and password > Save then launch
this could take a bit, so just take a little pause or grab a coffee while it's still scanning

Install a deprecated software and re-scan:
- Firefox contains 36 vulnerabilities; remediation >> upgrade to a newer version
- VLC contains 29 vulnerabilities; remediation >> upgrade to a newer version
- The system contains some vulnerabilities; remediation >> Apply Cumulative Update KB5010342.
- Microsoft Windows Defender; remediation >> Enable automatic updates

































Comments
Post a Comment